05
Nov
Industry-wide surveys indicate that nearly 60% of organizations have noticed an up tick in fraudulent emails. Over half of the respondents are not confident of their executives ability to detect this fraud. As a result, attempts at these type of attacks are only evolving and becoming more difficult to detect.
Certainly, the prevalence of attacks and the ignorance of their devices make for a dangerous scenario. First, we will go through the various types of attacks, and second go over what we can do to prevent them.
Deception.
This message purports to be from Microsoft threatening an account deactivation. If you hover over the destination link you’ll notice it is pointing to a random domain, but no mention of Microsoft.com or a related Office 365 domain you recognize is the red flag. Notice how they attempt to assuage your suspicion by stating at the bottom “We will not ask for payment information” – “Only your password”.
Spearphishing.
Compromised vendors or customers are typical sources of these attacks. You can expect to receive, for example, a new request for proposal from a website which will request a login for a well-known service (Office, Dropbox, Docusign are common). As a result of the relationship, the criminal will have an upper hand.
Whaling.
Domains similar to your own are registered; collettsystems.com becomes, for instance, col1ettsystems.com, colletsystems.com. With this, they attempt to trick you. Sensitive information is requested, and instructions to wire money to accounts is common and effective.
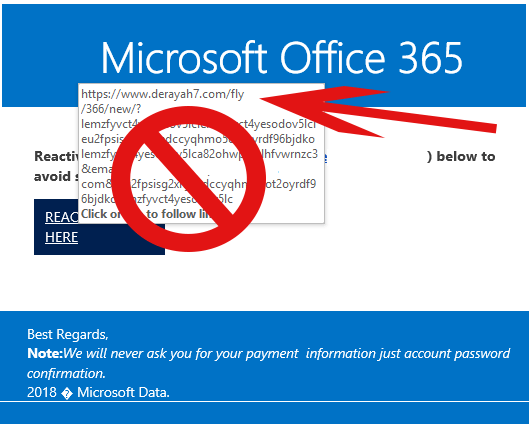
Notice the random domain name when you hover over the link.
Attacks can be prevented with proactive measures; for example:
First, companies should absolutely implement
DKIM (DomainKeys Identified Mail). DKIM cryptographically signs authorized mail so your recipient can verify that it is from who it purports to be. In addition, it certifies that it has not been modified in transit. After that,
SPF (Sender Policy Framework) needs to be implemented correctly as well. SPF designates permitted senders on the internet – when messages arrive that aren’t on that list, the receiving system knows that its very likely fraudulent.
Second, businesses should absolutely enable
two-factor authentication (2fa). Preferably, this will be company wide, but at least among your executive team. This requires a token which can be an app on your phone, SMS verification, or a separate hardware device. This is a changing token usually in the form of a six-digit number which is good for 30 seconds to a minute. Without both the password and that changing token access will be denied. It’s probably the most effective security precaution you can deploy.
Third, email users can opt to cryptographically sign messages. This is a seamless integration with Outlook. As a result of enabling this functionality, messages will arrive with a red ribbon seal icon, letting you know very quickly that an authorized sender which you our your IT has vetted previously sent that without any doubt.
Fourth, beware of any links that ask for personal information that come from email, and make sure you inspect the actual address if you’re receiving unsolicited documents and attachments
Finally, ensure your technical protection is up to par.
Managed Antivirus, Strong anti-spam measures are critical.



